Resources

[On-Demand Webinar] Why Threat Detection isn't Your Next DIY Project
You know what they say, “If you want it done right, you’ll just have to augment your existing cybersecurity team with Managed

[On-Demand Webinar] MDR Providers Decoded: Evaluating the Top 10 Capabilities your Provider Needs
Managed Detection and Response (MDR) services provide organizations with real-time threat detection, incident response, and co

[On-Demand Webinar] Cyber Threat Intelligence 101 Part 2: Building and Maturing Your Program
Getting information on recent vulnerabilities, malware and breaches is a priority – but is a constant challenge for many organ
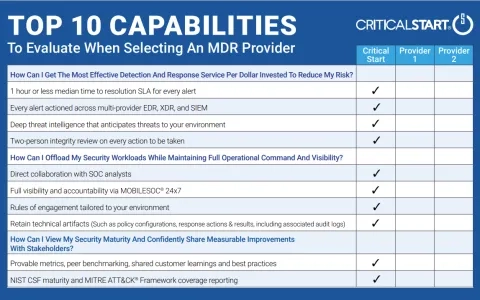
Top 10 Capabilities Checklist
Learn the top questions to ask and capabilities to evaluate when selecting an MDR provider

Eat Risk for Breakfast: Pancakes and Proactive Security
Watch Critical Start’s CSO, Jordan Mauriello, as he delves into the intricacies of monitoring risks, threats, and vulnerabilit
Critical Start Managed Detection and Response (MDR) Services for Palo Alto Networks® Cortex® Platforms
Critical Start MDR helps Palo Alto Networks Cortex clients reduce risk, mitigate breaches, and stop business disruption with 2

[On-Demand Webinar] Hunting for Threats: Lock & Load Your Organization with Managed Detection & Response
Explore the ever-changing threat landscape and delve into the art of securing your organization against cyberattacks with Crit

[On-Demand Webinar] Navigating the Cybersecurity Slopes: Unveiling the CRU's Innovative Approach
Watch the recording now!

Hunting for Cyber Threats
Watch the recording now:

[On-Demand Webinar] Security and Sneakers
Watch the recording now:

When MDRs See No Evil: How to Protect Your Organization from Undetected Threats
Watch Jim Rohde on-demand!

[On-Demand Webinar] Strategic Cyber Risk Management: A Proactive Approach for Sustainable Security
Today’s security and risk lead